A trader attracted to the cryptocurrency world could easily surmise that fraudsters have focused their efforts on the “big game”, so to speak. Yes, crooks know to concentrate their efforts where there are a multitude of potential targets to increase their probability for success. There are, however, a group of bad guys that are quite content to focus on the individual trader as their bread ticket. The form of schemes is not new. Criminals have adapted their “pet scams” to the digital world at hand and have gone a step further with new technology to ensure success. In these instances, you are your first and only line of defense when it comes to fraud prevention. Be aware, and be prepared!
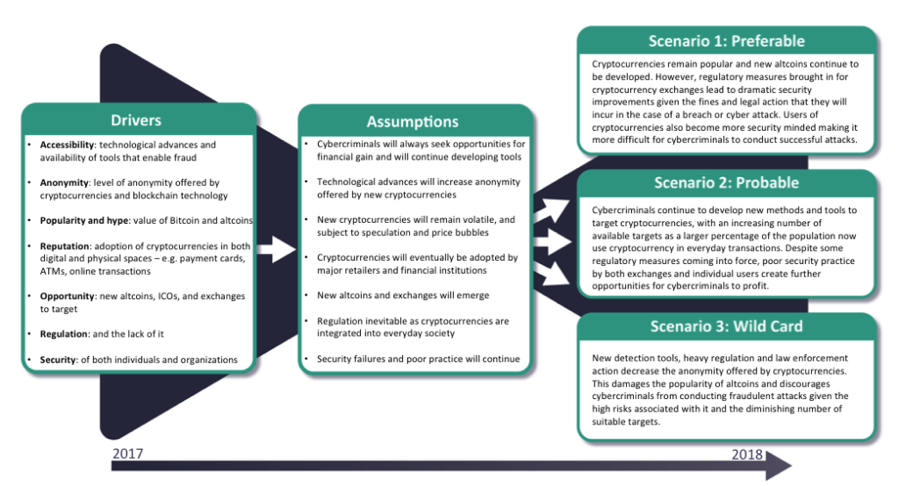
The diagram depicted above lays out a framework for probable scenarios in the cryptocurrency space that could lead to more protective regulation, all of which could be favorable for the industry. Fraud will not stop, for the individual trader will always be a target. The mechanisms have and will resemble other forms of forex trading, as follows:
- Price Manipulation: Every forex trader has dealt with price manipulation, slippage, and re-quotes, perhaps an early reason to consider changing brokers. Cryptocurrencies, however, have been called the most volatile asset class in history and for good reason. What may appear as fraud may not be, but if you are suspicious, a change may be in order;
- Fake Exchanges: Most every exchange is relatively new and un-relgulated. Traditional brokers, with a good history, are also joining the fray. Regulation may be a good thing, but it may make offshore exchanges or brokers look more appealing with better offers. Some may be fakes, but remember that trying to enforce your rights in a foreign jurisdiction is an exercise in futility;
- Account Takeovers: As difficult as it is to spot a fake exchange, it is just as difficult to discern if an email or URL link is a phony. Phishing expeditions are commonplace in the cryptoworld, because if a crook gains access to your access keys, then he can immediately transfer your balance and run. Malware installed on your PC is the modern way to compromise your privacy. Authentic looking emails that link you with a “clone” exchange site might ask you to log in to correct a setup issue. Social media has also become the conman’s playground, with fake ads and misleading offers. Do not fall for these types of come on;
- Credential Stuffing: The sad fact is that you may already be on a crook’s hit list. The process known as “Credential Stuffing” uses confiscated information, perhaps from a data breach of your exchange, and then using that data, without your knowledge, to rape and pillage accounts within the exchange. Unfortunately, the losses from this type of scam runs into the hundreds of millions of dollars;
- Mining Takeovers: The barrier for entry in the mining field is technical software knowledge, but primarily, you must have large budgets for computing power and the utility costs that enable them. Clever crooks have distributed malware to thousands of PCs, such that, when they turn the switch, they enlist the aid of their ill-intended global PC network. If your utility bill soars, you now know why;
- The Big Other: Never underestimate the cleverness of crooks to come up with a new ruse to tap into your account or trick you into transferring money to his illegitimate enterprise. Be skeptical, especially whenever you are tempted to respond to an email or link on the Internet. The fraudster’s first objective is to “set-the-hook”, which requires an action on your part. Avoid the temptation.
Why are we so susceptible these kinds of con game? As much as we hate to admit it, our own greed and gullibility play major roles. There is a psychology of fraud that con men use to their advantage, taking various behavioral factors and designing traps of persuasion that sound convincing. If we are to be saved, our intuitive minds must kick in to protect us, but that requires a framework of awareness upon which to work.
The simple message is be aware, be prepared, and be skeptical at all times.
